Why BF?
Irena Bojanova, PI & Lead, NIST Bugs Framework (BF), 2014 – ~~~~
Once fully developed, the Bugs Framework will have the expressiveness power to clearly describe any software bug or weakness, underlying any vulnerability. It is being built as a formal classification system that aims to augment the current state or the art weakness and vulnerability repositories:
- Common Weakness Enumeration (CWE) – a community-developed list of software and hardware weaknesses types.
- Common Vulnerabilities and Exposures (CVE) – a catalog of publicly disclosed cybersecurity vulnerabilities. Over 25,000 were documented in 2022 only.
- National Vulnerabilities Database (NVD) – the US government repository that links all CVEs to CWEs.
Repository Problems
CWE and CVE are widely used, but maybe difficult to use for comprehensive labeling of vulnerabilities. Their descriptions are in natural English language; they are not formal and may be imprecise or luck unclear causality. CWE also has gaps and overlaps in coverage.
- The following is an example of an imprecise CWE definition.
CWE-502: Deserialization of Untrusted Data: The application deserializes untrusted data without sufficiently verifying that the resulting data will be valid.
It’s not clear here what “sufficiently” means. “Verifying that data is valid” is also confusing. It should say “… without validating and verifying it”, as the validation and verification operations relate to syntax an semantics, correspondingly.
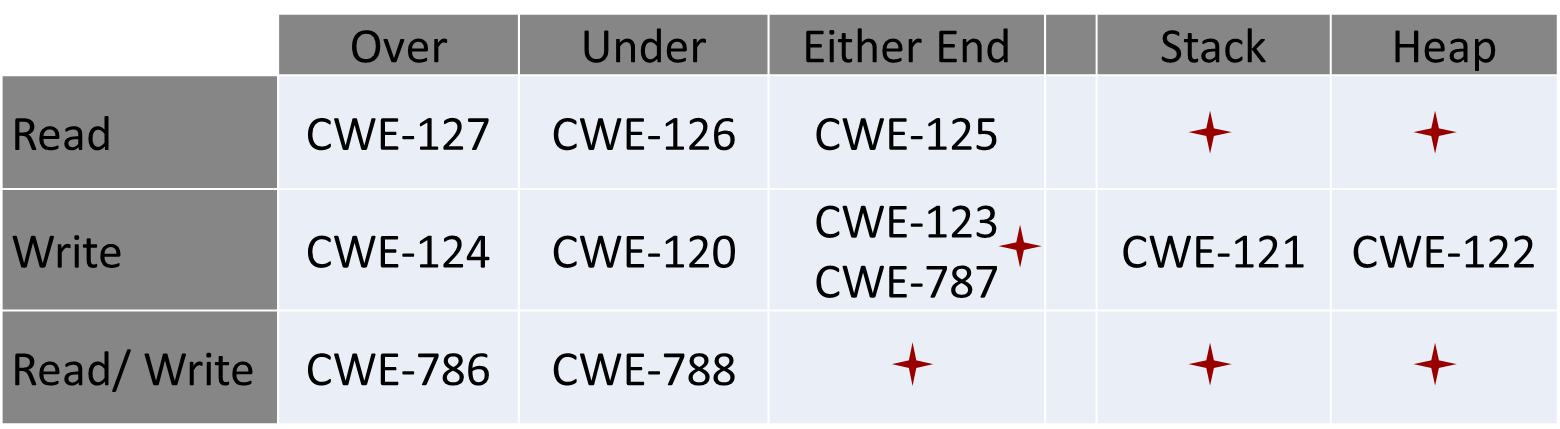
Gaps and overlaps in CWEs lead to confusion. As an example, if we arrange buffer overflow CWEs by read or write, over or under the bounds, on the stack or heap, the gaps and overlaps can be easily spotted.
Unclear causality in CVEs leads to wrong CWE assignments. For example, in this CVE, luck of input validation leads to integer overflow and then to buffer overflow.
CVE-2018-5907 : Possible buffer overflow in msm_adsp_stream_callback_put due to lack of input validation of user-provided data that leads to integer overflow in all Android releases (Android for MSM, Firefox OS for MSM, QRD Android) from CAF using the Linux kernel.
NVD labels it with CWE-190 – Integer Overflow or Wraparound, while the cause is CWE-20 – Improper Input Validation.
The full chain is: CWE 20 – CWE 190 – CWE 119, the last one being – Improper Restriction of Operations within the Bounds of a Memory Buffer.