BF Specification of CVE-2008-4539 “BitBlt” heap overflow in Cirrus VGA in KVM before kvm-82 and QEMU on Debian GNU/Linux and Ubuntu
-0.png)
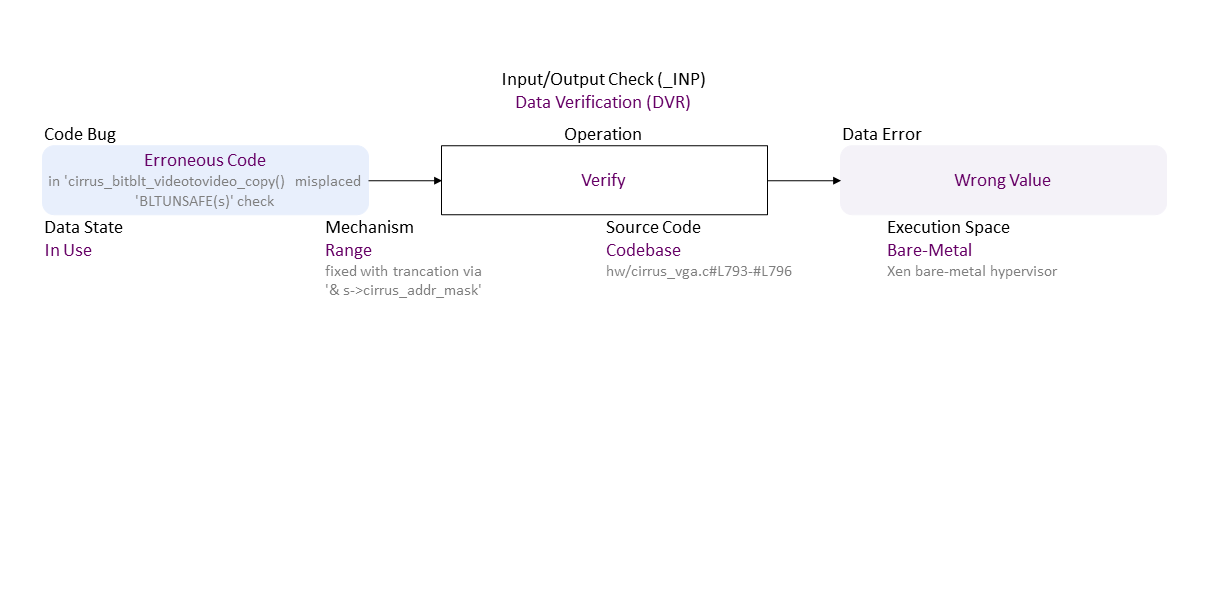
//generated// Erroneous Code (in ‘cirrus_bitblt_videotovideo_copy() misplaced ‘BLTUNSAFE(s)’ check) to Range Verify (fixed with trancation via ‘& s->cirrus_addr_mask’) In Use in Codebase (hw/cirrus_vga.c#L793-#L796) Bare-Metal (Xen bare-metal hypervisor) leads to Wrong Value
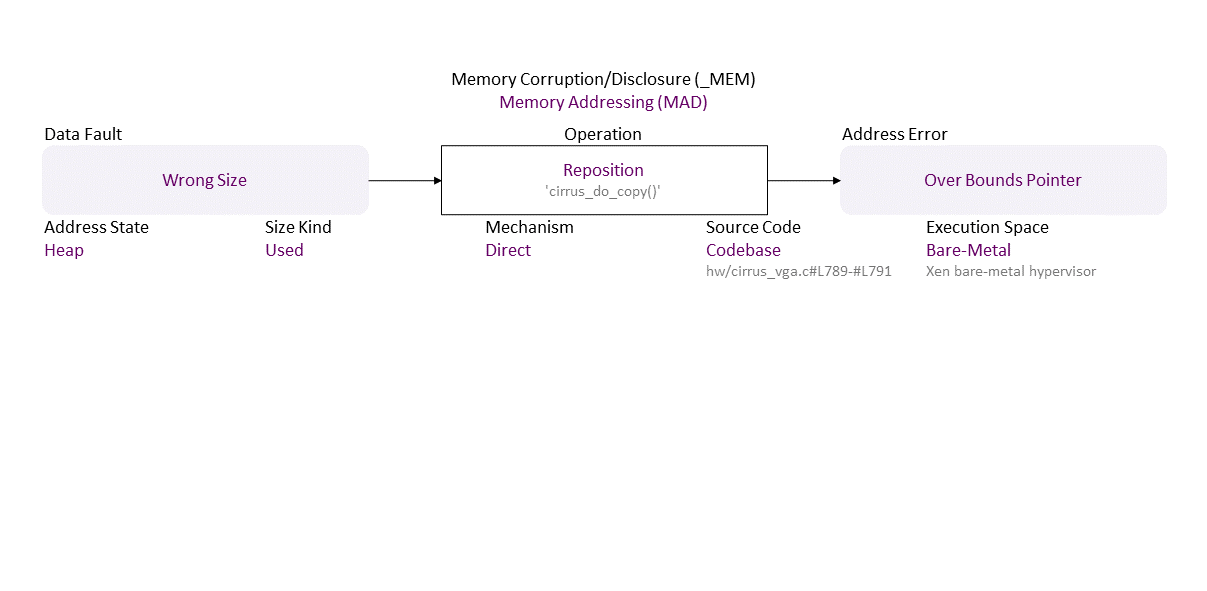
, which propagates to Wrong Size Direct Reposition (‘cirrus_do_copy()’) Heap Used Codebase (hw/cirrus_vga.c#L789-#L791) in Bare-Metal (Xen bare-metal hypervisor) resulting in Overbound Pointer
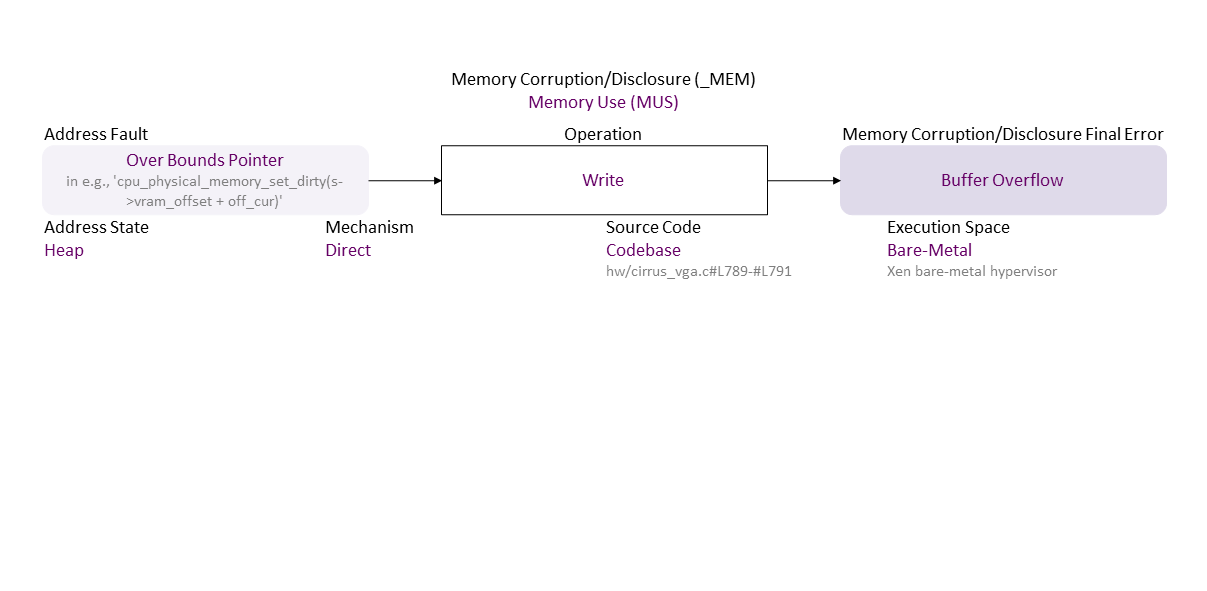
, which propagates to Overbound Pointer (in e.g., ‘cpu_physical_memory_set_dirty(s->vram_offset + off_cur)’) Direct Write Heap Codebase (hw/cirrus_vga.c#L789-#L791) in Bare-Metal (Xen bare-metal hypervisor) resulting in Buffer Overflow
. If exploited this can lead to ACE (everything could be lost).
|
|
| Class | Definition |
| DVR | Data Verification (DVR) class – Data are verified (i.e., semantics check) or corrected (i.e., assign or remove) improperly. |
| MAD | Memory Addressing (MAD) class – The pointer to an object is initialized, dereferenced, repositioned, or reassigned to an improper memory address. |
| MUS | Memory Use (MUS) class – An object is initialized, read, written, or cleared improperly. |
| Operation | Definition |
| Verify | Verify operation – Check data semantics (e.g., proper value/meaning) in order to accept (and possibly correct) or reject it. |
| Reposition | Reposition operation – Change the pointer to another position inside its object. |
| Write | Write operation – Change the data value of an object in memory to another meaningful value. |
| Cause/Consequence | Definition |
| Code Bug | Code Bug type – An error in the implementation of an operation – proper operands over an improper operation. A first cause for the chain of weaknesses underlying a software security vulnerability. Must be fixed to resolve the vulnerability. |
| Erroneous Code | Erroneous Code bug - There is a coding error in the implementation of the operation. |
| Data Error/Fault | Data Fault/Error type – The data of an object has harmed semantics or inconsistent or wrong value. |
| Wrong Value | Wrong Value fault/error – The data value is not accurate (e.g., outside of a range). |
| Wrong Size | Wrong Size fault/error – The value used as size or length (i.e., the number of elements) does not match an object's memory size or length (e.g., to limit a pointer reposition or index increment/decrement in a repetition statement). |
| Address Error/Fault | Address Fault/Error type – The address of an object is wrong. |
| Overbound Pointer | Overbound Pointer fault/error – Holds an address that is above the upper boundary of its object. |
| Memory Corruption/Disclosure Final Error | Memory Corruption/Disclosure final error type – An exploitable or undefined system behavior caused by memory addressing, allocation, use, or deallocation bugs. |
| Buffer Overflow | Buffer Overflow final error – Write data above the upper bound of an object (i.e., buffer overwrite). |
| Operation Attribute | Definition |
| Mechanism | Mechanism operation attribute type – Shows how the operation the operation with a bug or faulty operand is performed. |
| Range | Range operation attribute – The operation checks data are within a (min, max) interval. |
| Direct | Direct operation attribute – The operation is on a particular object element. |
| Source Code | Source Code operation attribute type – Shows where the code of the operation with a bug or faulty operand resides within the software, firmware, or hardware. |
| Codebase | Codebase operation attribute – The operation is in the programmer's code - in the application itself. |
| Execution Space | Execution Space operation attribute type – Shows where the operation with a bug or faulty operand is executed and the privilege level at which it runs. |
| Bare-Metal | Bare-Metal operation attribute – The bugged code runs in an environment without privilege control. Usually, the program is the only software running and has total access to the hardware. |
| Operand Attribute | Definition |
| Data State | Data State operand attribute type – Shows where the data comes from. |
| In Use | In Use operand attribute – Data are from a volatile storage (e.g., RAM, cache memory). |
| Address State | Address State operand attribute type – Shows where the address is (i.e., its location) in the memory layout. |
| Heap | |
| Size Kind | Size Kind operand attribute type – Shows what is used as the size or length (i.e., the number of elements) of an object - e.g., as the limit for traversal over the elements. |
| Used | Used operand attribute – A supplied value to be used as the size or length (i.e., the number of elements) of an object. |