BF Specification of CVE-2007-1320 BitBlt Heap Buffer Overflow
-0.png)
//generated//
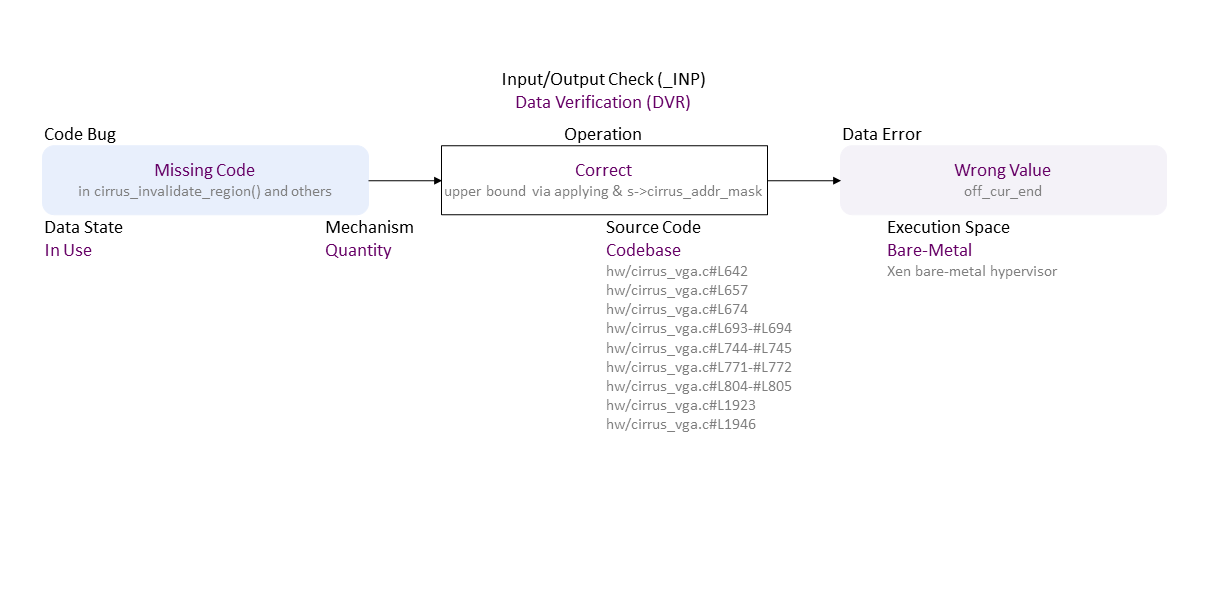
Missing Code (in cirrus_invalidate_region() and others) to Quantity Correct upper bound via applying & s->cirrus_addr_mask In Use in Codebase (hw/cirrus_vga.c#L642
hw/cirrus_vga.c#L642
hw/cirrus_vga.c#L657
hw/cirrus_vga.c#L674
hw/cirrus_vga.c#L693-#L694
hw/cirrus_vga.c#L744-#L745
hw/cirrus_vga.c#L771-#L772
hw/cirrus_vga.c#L804-#L805
hw/cirrus_vga.c#L1923
hw/cirrus_vga.c#L1946) Bare-Metal (Xen bare-metal hypervisor) leads to Wrong Value (off_cur_end)
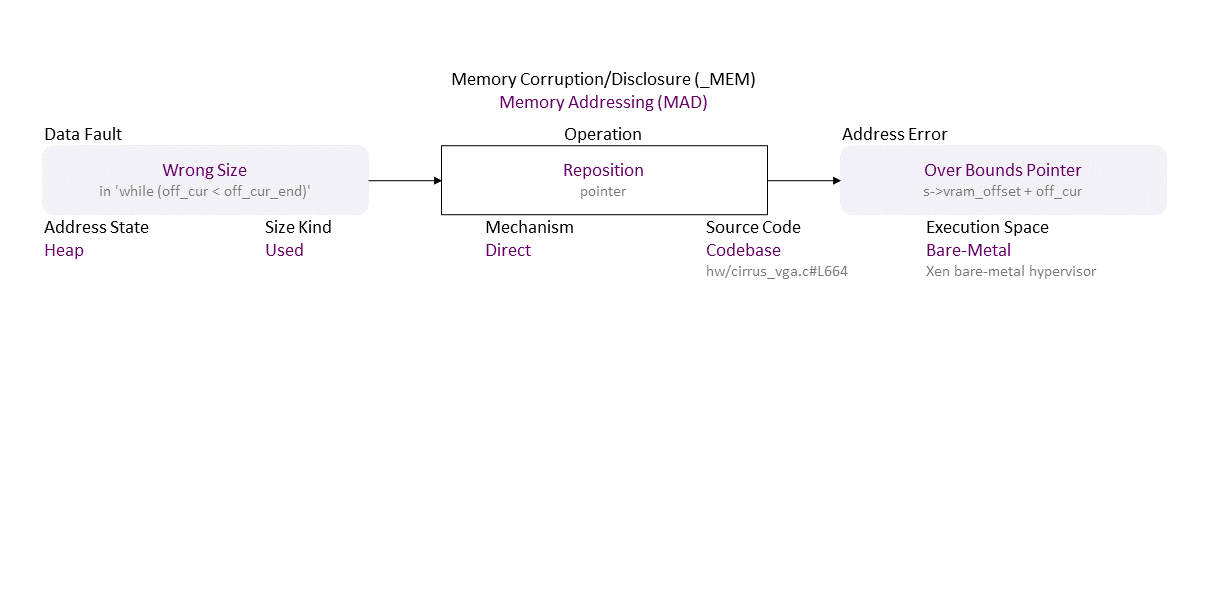
, which propagates to Wrong Size (in ‘while (off_cur < off_cur_end)’) Direct Reposition (pointer) Heap Used Codebase (hw/cirrus_vga.c#L664) in Bare-Metal (Xen bare-metal hypervisor) resulting in Over Bounds Pointer (s->vram_offset + off_cur)
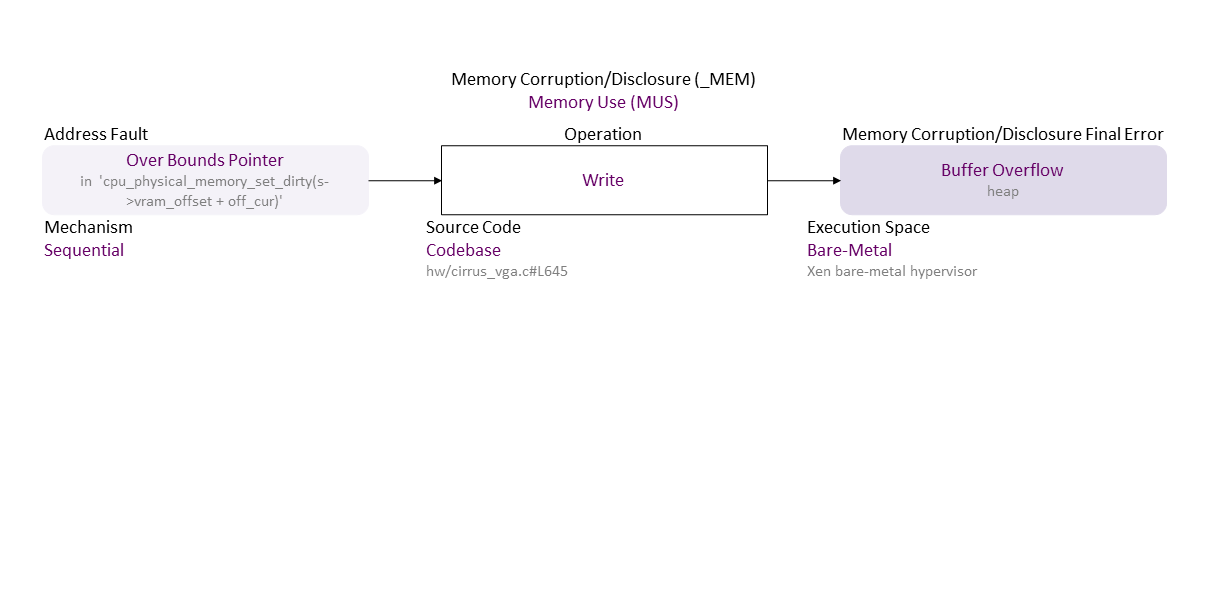
, which propagates to Over Bounds Pointer (in ‘cpu_physical_memory_set_dirty(s->vram_offset + off_cur)’) Sequential Write Codebase (hw/cirrus_vga.c#L645) in Bare-Metal (Xen bare-metal hypervisor) resulting in Buffer Overflow (heap)
. If exploited this can lead to ACE (everything could be lost).
vendor:product: qemu:qemu |
|
|
|
| Class | Definition |
| DVR | Data Verification (DVR) class – Data are verified (semantics check) or corrected (assign, remove) improperly. |
| MAD | Memory Addressing (MAD) class – The pointer to an object is initialized, repositioned, or reassigned to an improper memory address. |
| MUS | Memory Use (MUS) class – An object is initialized, read, written, or cleared improperly. |
| Operation | Definition |
| Correct | Correct operation – Modify data (assign new value, remove) to make it accurate. |
| Reposition | Reposition operation – Change the pointer to another position inside its object. |
| Write | Write operation – Change the data value of an object to another meaningful value. |
| Cause/Consequence | Definition |
| Code Bug | Code Bug type – Defect in the implementation of the operation – proper operands over an improper operation. A first cause for the chain of weaknesses underlying a software security vulnerability. Must be fixed to resolve the vulnerability. |
| Missing Code | Missing Code bug - The operation is entirely absent. |
| Data Error/Fault | Data Fault/Error type – The object data has harmed semantics or inconsistent or wrong value. |
| Wrong Value | Wrong Value fault/error – The value of the data is not accurate (e.g., outside of a range). |
| Wrong Size | Wrong Size fault/error – The value used as size does not match the actual size of the object (e.g., to restrict pointer repositioning or index increment/decrement in a repetition statement). |
| Address Error/Fault | Address Fault/Error type – The object address in use is wrong. |
| Over Bounds Pointer | Over Bounds Pointer fault/error – Holds an address above the upper boundary of its object. |
| Memory Corruption/Disclosure Final Error | Memory Corruption/Disclosure exploitable error type – An exploitable or undefined system behavior caused by memory addressing, allocation, use, and deallocation bugs. |
| Buffer Overflow | Buffer Overflow exploitable error – Writing above the upper bound of an object – aka Buffer Over-Write. |
| Operation Attribute | Definition |
| Mechanism | Mechanism operation attribute type – Shows how the buggy/faulty operation code is performed. |
| Quantity | Quantity operation attribute – The operation checks data for a specific measurable value (e.g., size, time, rate, frequency). |
| Direct | Direct operation attribute – The operation is on a particular object element. |
| Sequential | Sequential operation attribute – The operation is via iterating over the object elements. |
| Source Code | Source Code operation attribute type – Shows where the operation with the bug or a faulty operand is in the program – in what kind of software. |
| Codebase | Codebase operation attribute – The operation is in the programmer's code - in the application itself. |
| Execution Space | Execution Space operation attribute type – Shows where the buggy/faulty operation code is running or with what privilege level. |
| Bare-Metal | Bare-Metal operation attribute – The bugged code runs in an environment without privilege control. Usually, the program is the only software running and has total access to the hardware. |
| Operand Attribute | Definition |
| Data State | Data State operand attribute type operand attribute – Shows where the data come from. |
| In Use | In Use operand attribute – Data are from a volatile storage (e.g., RAM, cache memory). |
| Address State | Address State operand attribute type - State operand attribute type – Shows where the address is in the memory layout. |
| Heap | Heap operand attribute – The object is a dynamically allocated data structure (e.g., via malloc() and new). |
| Size Kind | Size Kind operand attribute type – Shows what the limit for traversal of the object is. |
| Used | Used operand attribute – A supplied size for an object. |