BF Specification of CVE-2007-6429 Integer overflows in X.Org Xserver before 1.4.1
-0.png)
Missing verifications of input values leads to use of a wrong argument in a memory size calculations and wraparounds , allowing allocation of not enough memory, which, when used leads to a buffer overflow. If exploited, this can lead to arbitrary code execution.
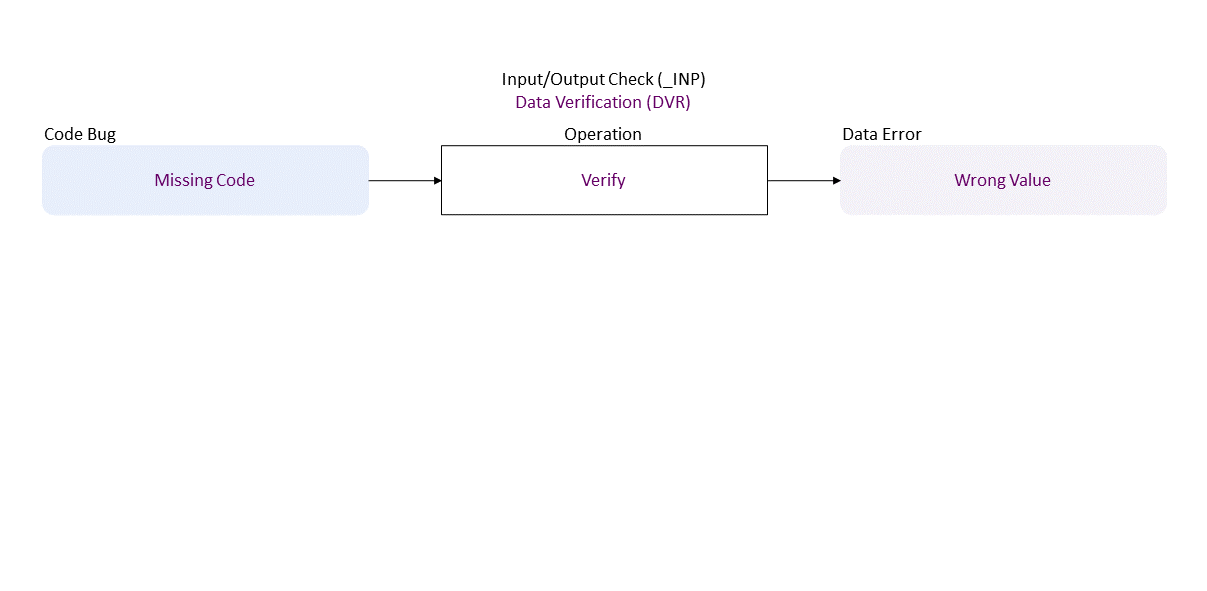
//generated// Missing Code to Verify in leads to Wrong Value
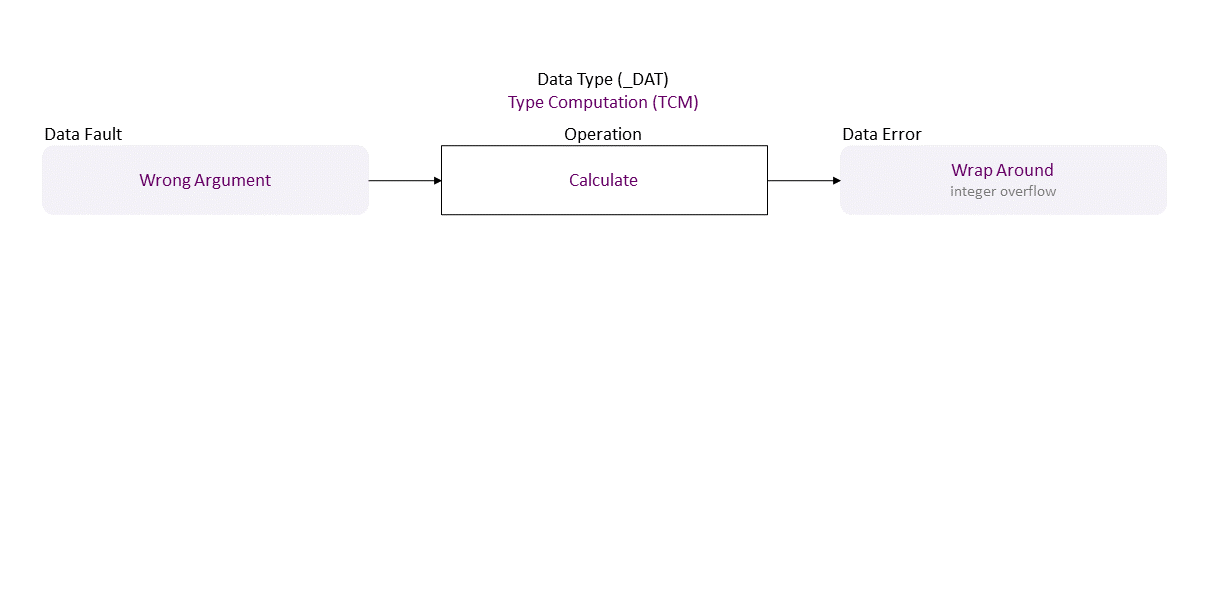
, which propagates to Wrong Argument Calculate in resulting in Wrap Around (integer overflow)
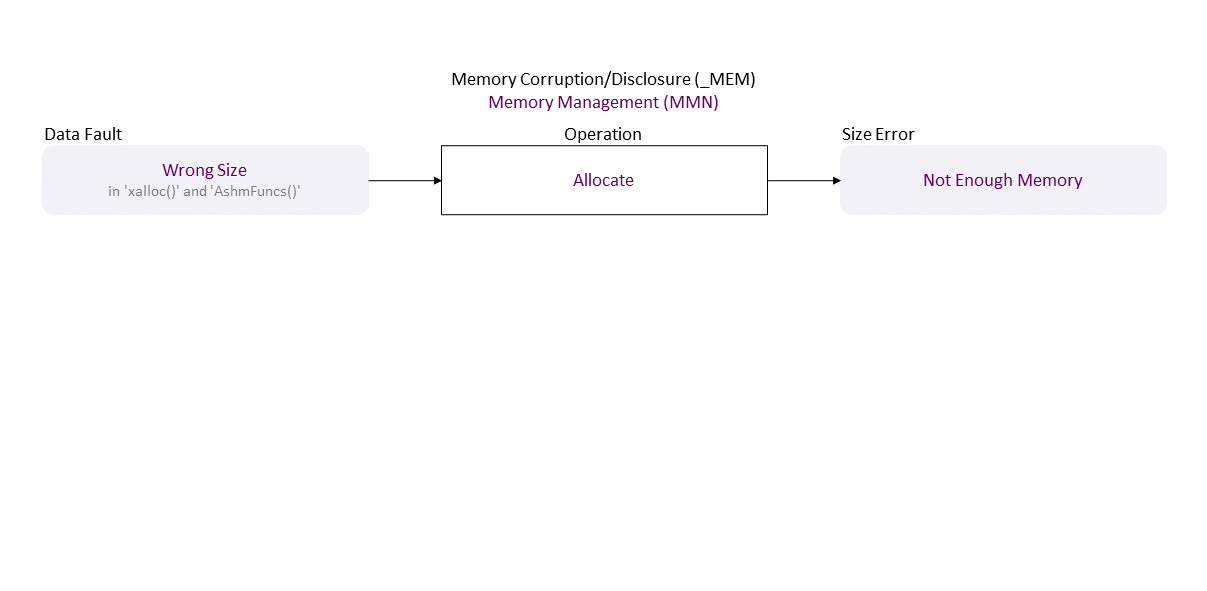
, which propagates to Wrong Size (in ‘xalloc()’ and ‘AshmFuncs()’) Allocate in resulting in Not Enough Memory
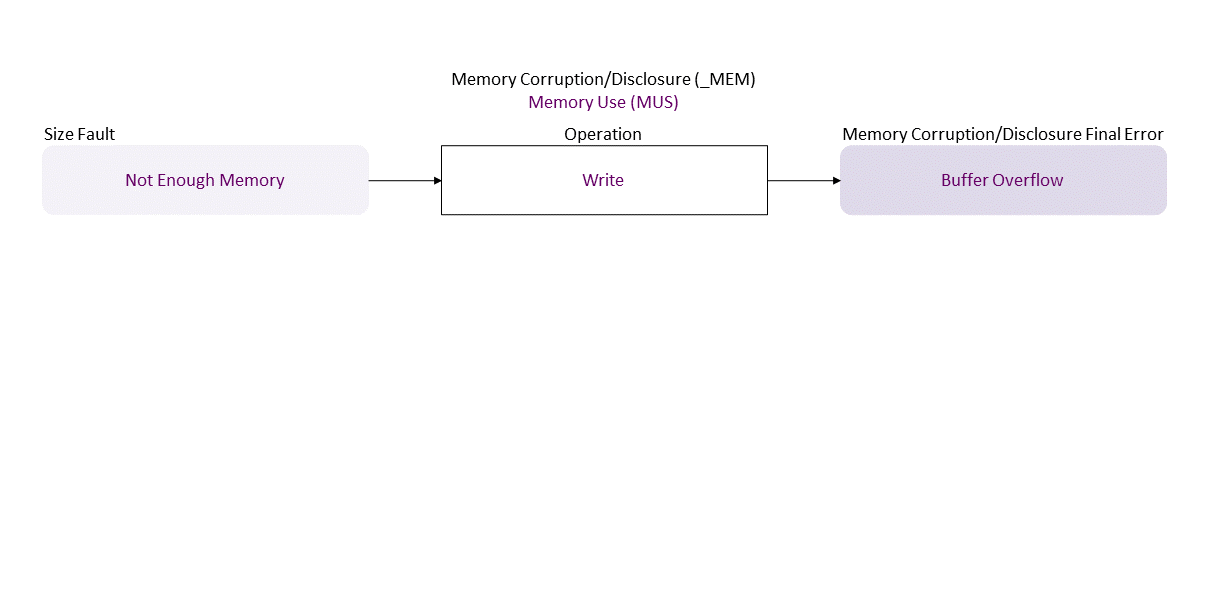
, which propagates to Not Enough Memory Write in resulting in Buffer Overflow
. If exploited this can lead to ACE (everything could be lost).
vendor:product: x.org:evi |
|
| Class | Definition |
| DVR | Data Verification (DVR) class – Data are verified (semantics check) or corrected (assign, remove) improperly. |
| TCM | Type Computation (TCM) class – An arithmetic expression (over numbers, strings, or pointers) is calculated improperly, or a boolean condition is evaluated improperly. |
| MMN | Memory Management (MMN) class – An object is allocated, deallocated, or resized improperly. |
| MUS | Memory Use (MUS) class – An object is initialized, read, written, or cleared improperly. |
| Operation | Definition |
| Verify | Verify operation – Check data semantics (proper value/meaning) in order to accept (and possibly correct) or reject it. |
| Calculate | Calculate operation – Find the result of a numeric, pointer, or string operation. |
| Allocate | Allocate operation – Reserve space in memory for an object; defines its initial boundaries and size. |
| Write | Write operation – Change the data value of an object to another meaningful value. |
| Cause/Consequence | Definition |
| Code Bug | Code Bug type – Defect in the implementation of the operation – proper operands over an improper operation. A first cause for the chain of weaknesses underlying a software security vulnerability. Must be fixed to resolve the vulnerability. |
| Missing Code | Missing Code bug - The operation is entirely absent. |
| Data Error/Fault | Data Fault/Error type – The object data has harmed semantics or inconsistent or wrong value. |
| Wrong Value | Wrong Value fault/error – The value of the data is not accurate (e.g., outside of a range). |
| Wrong Argument | Wrong Argument fault/error – Inaccurate input data value, i.e., non-verified for harmed semantics. |
| Wrap Around | Wrap Around fault/error – A moved around-the-clock value over its data type upper or lower range, as it exceeds that range. (Integer Over-/Under-flow is a wrapped-around the upper/lower range integer value; may become very small/large and change to the opposite sign. |
| Wrong Size | Wrong Size fault/error – The value used as size does not match the actual size of the object (e.g., to restrict pointer repositioning or index increment/decrement in a repetition statement). |
| Size Error/Fault | Size Fault/Error type – The object size in use is wrong. |
| Not Enough Memory | Not Enough Memory fault/error – The allocated memory is too little for the data it should store. |
| Memory Corruption/Disclosure Final Error | Memory Corruption/Disclosure exploitable error type – An exploitable or undefined system behavior caused by memory addressing, allocation, use, and deallocation bugs. |
| Buffer Overflow | Buffer Overflow exploitable error – Writing above the upper bound of an object – aka Buffer Over-Write. |
| Operation Attribute | Definition |
| Operand Attribute | Definition |