BF Specification of CVE-2013-4934 Wireshark v1.8.x before v1.8.9 and v1.10.x before v1.10.1
-0.png)
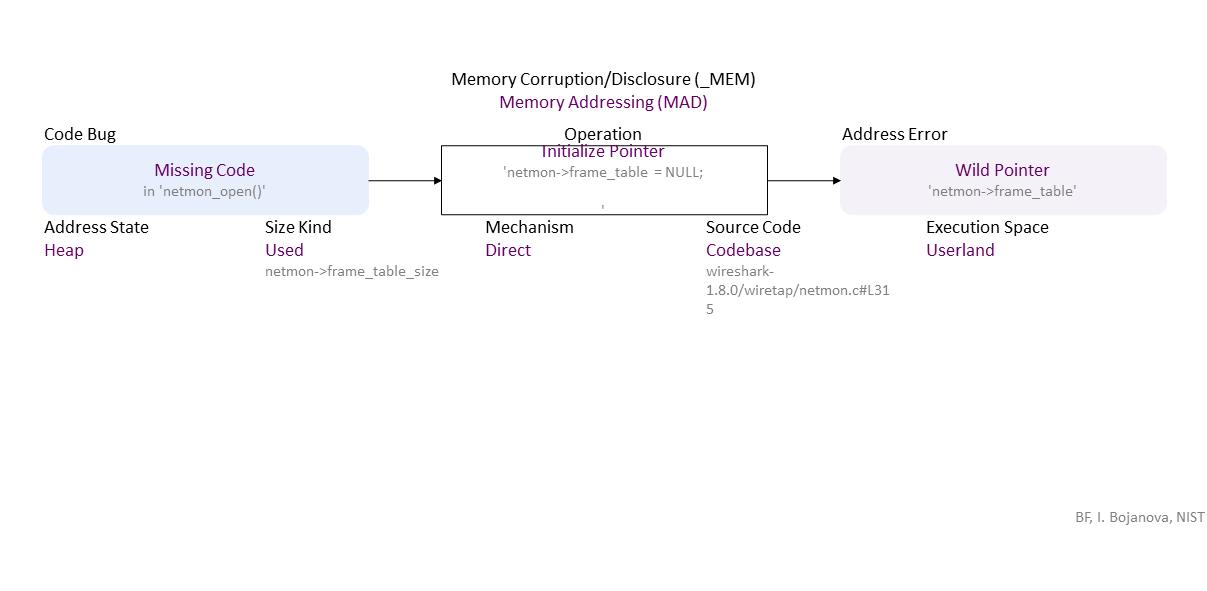
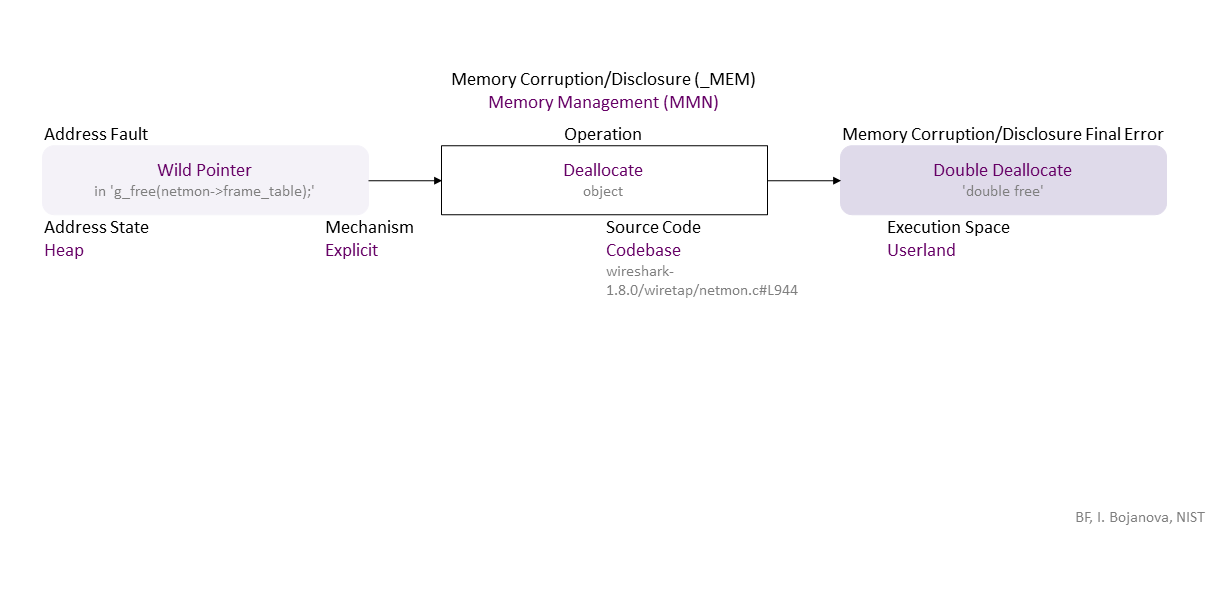
Missing direct initialization of the 'netmon->frame_table' pointer to NULL leads to a wild pointer, which, when used for explicit deallocation of its object on the heap leads to a double deallocate (double free). If exploited, this can lead to denial of service (DOS) and more specifically application crash-- availability loss.
//generated// Missing Code (in ’netmon_open()’) to Direct Initialize Pointer ’netmon->frame_table = NULL;’ Heap Used (netmon->frame_table_size) in Codebase (wireshark-1.8.0/wiretap/netmon.c#L315) Userland leads to Wild Pointer (’netmon->frame_table')
, which propagates to Wild Pointer (in ‘g_free(netmon->frame_table);’) Explicit Deallocate (object) Heap Codebase (wireshark-1.8.0/wiretap/netmon.c#L944) in Userland that results in Double Deallocate (‘double free’)
, which can be exploited toward DOS (availability loss) – application crash) security failure.
|
| Class | Definition |
| MAD | Memory Addressing (MAD) class – The pointer to an object is initialized, dereferenced, repositioned, or reassigned to an improper memory address. |
| MMN | Memory Management (MMN) class – An object is allocated, resized, or deallocated improperly. |
| Operation | Definition |
| Initialize Pointer | Initialize Pointer operation – Change the undefined data value of a pointer to a meaningful object address; and position the pointer at the start of the object. |
| Deallocate | Deallocate operation – Release the allocated memory of an object. |
| Cause/Consequence | Definition |
| Code Bug | Code Bug type – An error in the implementation of an operation – proper operands over an improper operation. It is the roor cause of a security vulnerability. Must be fixed to resolve the vulnerability. |
| Missing Code | Missing Code bug - The operation is misplaced entirely absent. |
| Address Error/Fault | Address Fault/Error type – The address of an object is wrong. |
| Wild Pointer | Wild Pointer fault/error – Holds an arbitrary address, because it has not been initialized or an erroneous allocation routine was used. |
| Memory Corruption/Disclosure Final Error | Memory Corruption/Disclosure final error type – An exploitable or undefined system behavior caused by memory addressing, allocation, use, or deallocation bugs. |
| Double Deallocate | Double Deallocate final error – An attempt to deallocate a deallocated (freed) object. |
| Operation Attribute | Definition |
| Mechanism | Mechanism operation attribute type – Shows how the operation the operation with a bug or faulty operand is performed. |
| Direct | Direct operation attribute – The operation is on a particular object element. |
| Explicit | Explicit operation attribute – The operation is via a function/method call. |
| Source Code | Source Code operation attribute type – Shows where the code of the operation with a bug or faulty operand resides within the software, firmware, or hardware. |
| Codebase | Codebase operation attribute – The operation is in the programmer's code - in the application itself. |
| Execution Space | Execution Space operation attribute type – Shows where the operation with a bug or faulty operand is executed and the privilege level at which it runs. |
| Userland | Userland operation attribute – The bugged code runs in an environment with privilege levels, but in unprivileged mode (e.g., ring 3 in x86 architecture). |
| Operand Attribute | Definition |
| Address State | Address State operand attribute type – Shows where the address is (i.e., its location) in the memory layout. |
| Heap | The object is a dynamically allocated data structure (e.g., via malloc() and new). |
| Size Kind | Size Kind operand attribute type – Shows what is used as the size or length (i.e., the number of elements) of an object - e.g., as the limit for traversal over the elements. |
| Used | Used operand attribute – A supplied value to be used as the size or length (i.e., the number of elements) of an object. |