BF Specification of CVE-2023-3765 File Injection (absolute path traversal) in GitHub MLflow before v2.5.0
-0.png)
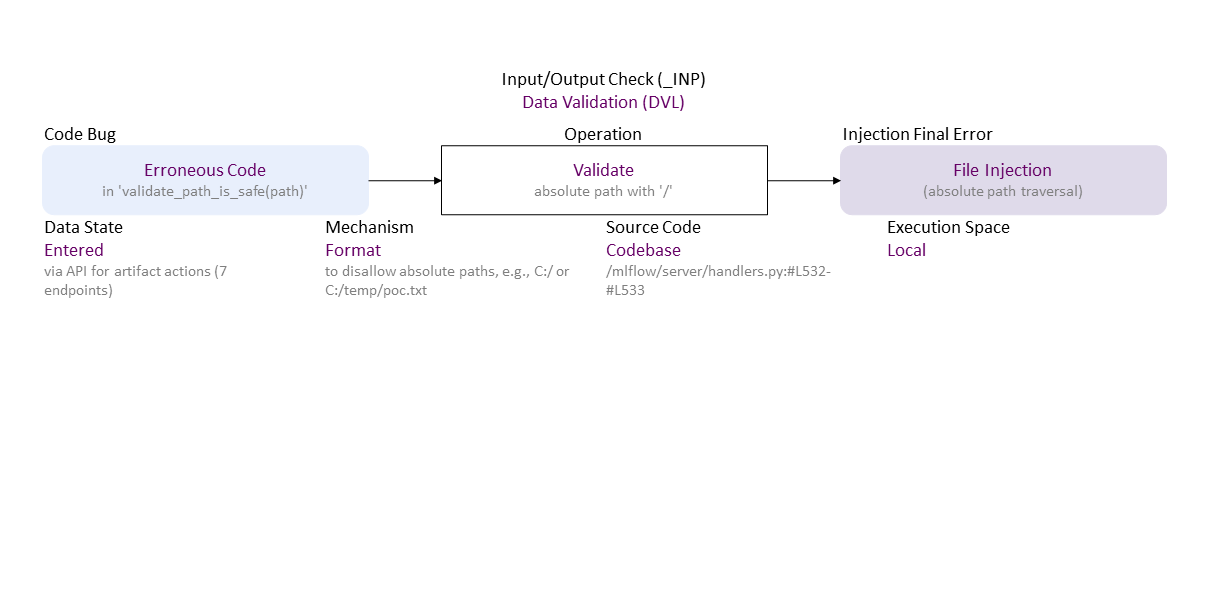
Erroneous validation (does not check for absolute path format with '/', e.g. C:/ or C:/temp/poc.txt) in validate_path_is_safe() leads to file injection -- absolute path traversal. If exploited, this can lead to information exposure, data tempering, or denial of service -- confidentiality, integrity, and availability loss, correspondingly.//generated//
Erroneous Code (in 'validate_path_is_safe(path)') to Format Validate absolute path with '/' (to disallow absolute paths, e.g., C:/ or C:/temp/poc.txt) Entered (via API for artifact actions (7 endpoints)) in Codebase (/mlflow/server/handlers.py:#L532-#L533) Local leads to File Injection ((absolute path traversal)). If exploited this can lead to IEX (confidentiality loss) or DOS (availability loss) or TPR (integrity loss).
vendor:product: lfprojects:mlflow |
| Class | Definition |
| DVL | Data Validation (DVL) class – Data are validated (syntax check) or sanitized (escape, filter, repair) improperly. |
| Operation | Definition |
| Validate | Validate operation – Check data syntax (proper form/grammar, incl. check for missing symbols/elements) in order to accept (and possibly sanitize) or reject it. |
| Cause/Consequence | Definition |
| Code Bug | Code Bug type – Defect in the implementation of the operation – proper operands over an improper operation. A first cause for the chain of weaknesses underlying a software security vulnerability. Must be fixed to resolve the vulnerability. |
| Erroneous Code | Erroneous Code bug - There is a coding error in the implementation of the operation. |
| Injection Final Error | Injection exploitable error type – An exploitable or undefined system behavior caused by 'code separation' data validation bugs. |
| File Injection | File Injection exploitable error – Maliciously inserted data (e.g., with .. and / or with file entries) into an input used to access/modify files or as a file content. |
| Operation Attribute | Definition |
| Mechanism | Mechanism operation attribute type – Shows how the buggy/faulty operation code is performed. |
| Format | Format operation attribute – The operation is via a policy based on syntax format (e.g., defined via regular expression). |
| Source Code | Source Code operation attribute type – Shows where the operation with the bug or a faulty operand is in the program – in what kind of software. |
| Codebase | Codebase operation attribute – The operation is in the programmer's code - in the application itself. |
| Execution Space | Execution Space operation attribute type – Shows where the buggy/faulty operation code is running or with what privilege level. |
| Local | Local operation attribute – The bugged code runs in an environment with access control policy with limited (local user) permission. |
| Operand Attribute | Definition |
| Data State | Data State operand attribute type operand attribute – Shows where the data come from. |
| Entered | Entered operand attribute – Data are from a user via a user interface (e.g., input field of a dialog or a command prompt). |