BF Specification of CVE-2015-5221 — Use-after-free in JasPer JPEG-2000 before 1.900.2
-0.png)
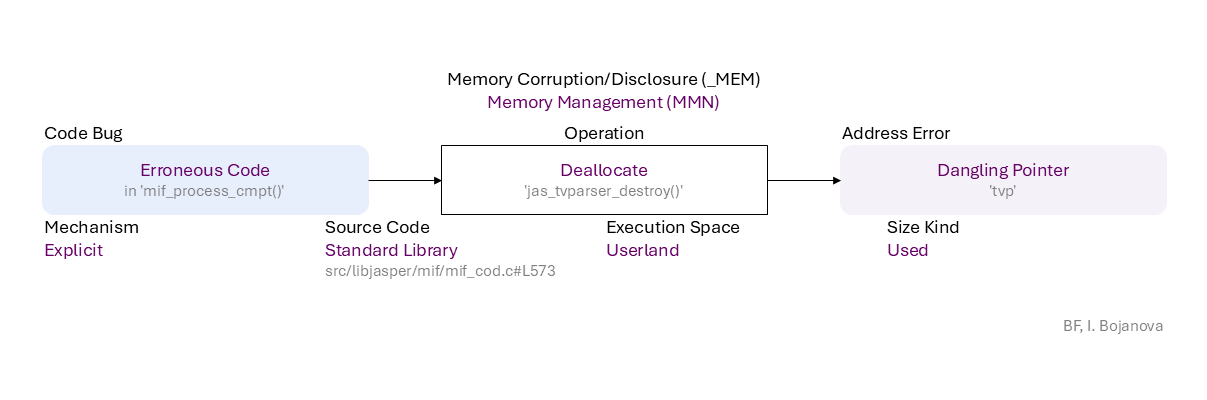
Erroneous Code (in 'mif_process_cmpt()') to Deallocate ('jas_tvparser_destroy()') with Used size using Explicit mechanism in Standard Library source code (src/libjasper/mif/mif_cod.c#L573) in Userland execution space leads to Dangling Pointer ('tvp') error, which propagates to
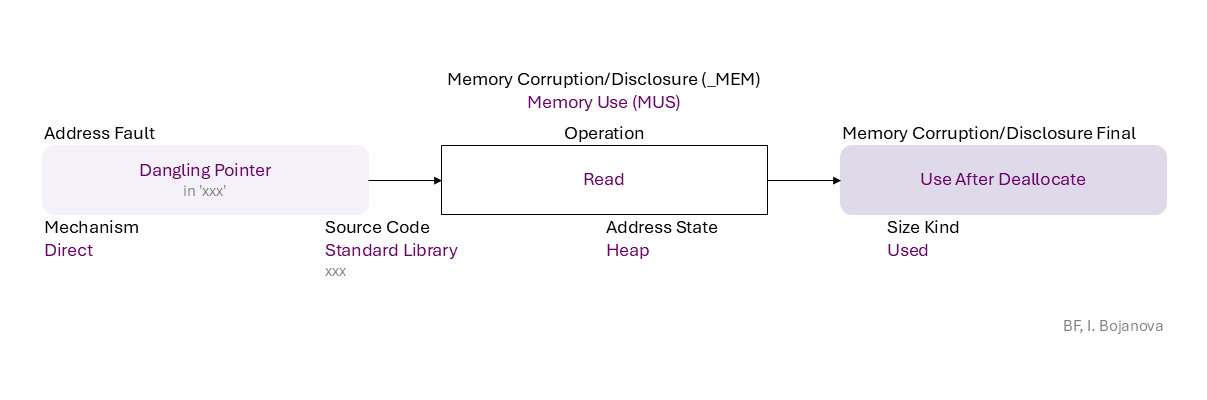
Dangling Pointer (in 'xxx') to Read on Heap with Used size using Direct mechanism in Standard Library source code (xxx) that results in Use After Deallocate final error, which can be exploited toward
Denial of Service (DOS) (availability loss) security failure.
|
|
| Class | Definition |
| MMN | Memory Management (MMN) class – An object is allocated, resized, or deallocated improperly. |
| MUS | Memory Use (MUS) class – An object is initialized, read, written, or cleared improperly. |
| Operation | Definition |
| Deallocate | Deallocate operation – Release the allocated memory of an object. |
| Read | Read operation – Retrieve the data value of an object from memory. |
| Cause/Consequence | Definition |
| Code Bug | Code Bug type – An error in the implementation of an operation – proper operands over an improper operation. It is the roor cause of a security vulnerability. Must be fixed to resolve the vulnerability. |
| Erroneous Code | Erroneous Code bug - There is a coding error in the implementation of the operation. |
| Address Error/Fault | Address error (or fault) type – The address of an object is wrong. |
| Dangling Pointer | Dangling Pointer error (or fault) – Still holds the address of its successfully deallocated object (e.g., a pointer to a freed heap object or address of a stack object returned by a function). |
| Memory Corruption/Disclosure Final Error | Memory Corruption/Disclosure final error/exploit vector type – An exploitable or undefined system behavior caused by memory addressing, allocation, use, or deallocation bugs. |
| Use After Deallocate | use after free or use after return) final error – An attempt to use (dereference, read, write, or clear) a deallocated object (e.g., via a pointer to a freed or reallocated heap object -- use after free) or out of scope object (e.g., via a returned by a function pointer to a stack object -- use after return). |
| Operation Attribute | Definition |
| Mechanism | Mechanism operation attribute type – Shows how the operation with a bug or faulty operand is performed. |
| Explicit | Explicit operation attribute – The operation is via a function/method call. |
| Direct | Direct operation attribute – The operation is on a particular object element. |
| Source Code | Source Code operation attribute type – Shows where the code of the operation with a bug or faulty operand resides within the software, firmware, or hardware. |
| Standard Library | Standard Library operation attribute – The operation code is in the standard library for a particular programming language. |
| Execution Space | Execution Space operation attribute type – Shows where the operation with a bug or faulty operand is executed and the privilege level at which it runs. |
| Userland | Userland operation attribute – The bugged code runs in an environment with privilege levels, but in unprivileged mode (e.g., ring 3 in x86 architecture). |
| Operand Attribute | Definition |
| Size Kind | Size Kind operand attribute type – Shows what is used as the size or length (i.e., the number of elements) of an object - e.g., as the limit for traversal over the elements. |
| Used | Used operand attribute – A supplied value to be used as the size or length (i.e., the number of elements) of an object. |
| Address State | Address State operand attribute type – Shows where the address is (i.e., its location) in the memory layout. |
| Heap | The object is a dynamically allocated data structure (e.g., via malloc() or new). |
| Failure | Definition |
| DOS | Denial of Service (DOS) – Disruption of access to or use of information or information systems that leads to availability loss. |