BF Specification of CVE-2023-1283 — Code Injection in GitHub repository builderio/qwik prior to 0.21.0.
-0.png)
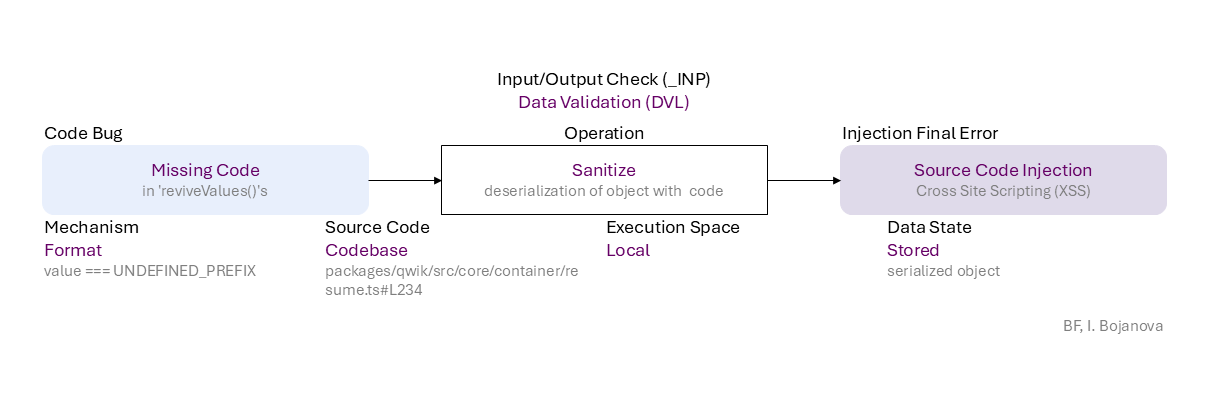
Missing Code (in 'reviveValues()'s) to Sanitize (deserialization of object with code) of Stored data (serialized object) using Format mechanism (value === UNDEFINED_PREFIX) in Codebase source code (packages/qwik/src/core/container/resume.ts#L234) in Local execution space leads to Source Code Injection (Cross Site Scripting (XSS)) final error, which can be exploited toward
Arbitrary Code Execution (ACE) (everything could be lost) security failure.
|
| Class | Definition |
| DVL | Data Validation (DVL) class – Data are validated (i.e., syntax check) or sanitized (i.e., escape, filter, or repair) improperly. |
| Operation | Definition |
| Sanitize | Sanitize operation – Modify data (e.g., escape/neutralize, filter/remove, or repair/add symbols or elements) to make it valid (well-formed). |
| Cause/Consequence | Definition |
| Code Bug | Code Bug type – An error in the implementation of an operation – proper operands over an improper operation. It is the roor cause of a security vulnerability. Must be fixed to resolve the vulnerability. |
| Missing Code | Missing Code bug - The operation is misplaced entirely absent. |
| Injection Final Error | Injection final error/exploit vector type – An exploitable or undefined system behavior caused by validation or sanitization bugs. |
| Source Code Injection | Source Code Injection final error – Maliciously inserted new code (incl. with <> elements) into an input used as a part of an executing application code. |
| Operation Attribute | Definition |
| Mechanism | Mechanism operation attribute type – Shows how the operation with a bug or faulty operand is performed. |
| Format | Format operation attribute – The operation is via a policy based on syntax format (e.g., defined via regular expression). |
| Source Code | Source Code operation attribute type – Shows where the code of the operation with a bug or faulty operand resides within the software, firmware, or hardware. |
| Codebase | Codebase operation attribute – The operation is in the programmer's code - in the application itself. |
| Execution Space | Execution Space operation attribute type – Shows where the operation with a bug or faulty operand is executed and the privilege level at which it runs. |
| Local | Local operation attribute – The bugged code runs in an environment with access control policy with limited (local user) permission. |
| Operand Attribute | Definition |
| Data State | Data State operand attribute type – Shows where the data comes from. |
| Stored | Stored operand attribute – Data are from a permanent storage (e.g., file, database on a storage device); they are at rest. |
| Failure | Definition |
| ACE | Arbitrary Code Execution (ACE) – Execution of unauthorized commands or code execution that could lead to everything being lost; remote code execution (RCE) is a sub-case of ACE on a target system or device from a remote location, typically over a network. |