BF Specification of CVE-2023-3765 — File Injection (absolute path traversal) in GitHub MLflow before v2.5.0
-0.png)
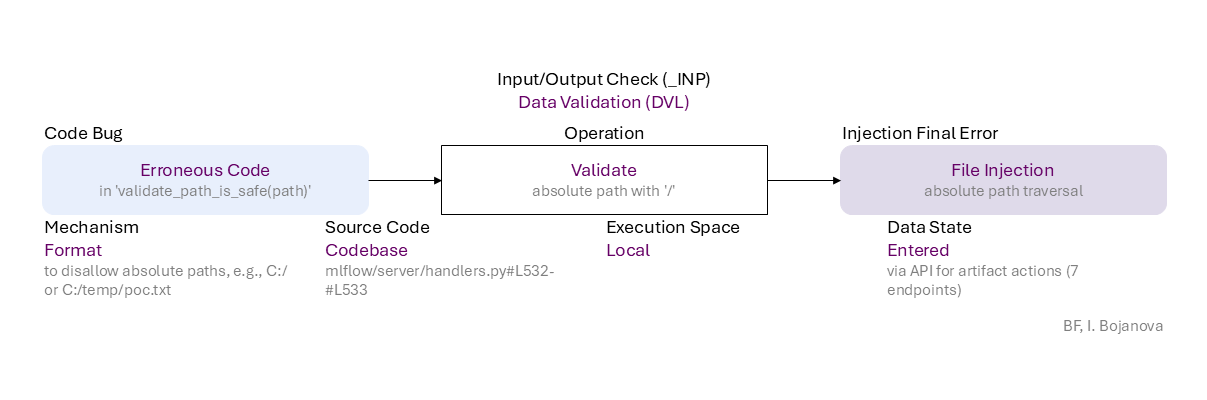
Erroneous validation (does not check for absolute path format with '/', e.g. C:/ or C:/temp/poc.txt) in validate_path_is_safe() leads to file injection -- absolute path traversal. If exploited, this can lead to information exposure, data tempering, or denial of service -- confidentiality, integrity, and availability loss, correspondingly.
Erroneous Code (in 'validate_path_is_safe(path)') to Validate (absolute path with '/') of Entered data (via API for artifact actions (7 endpoints)) using Format mechanism (to disallow absolute paths, e.g., C:/ or C:/temp/poc.txt) in Codebase source code (mlflow/server/handlers.py#L532-#L533) in Local execution space leads to File Injection (absolute path traversal) final error, which can be exploited toward
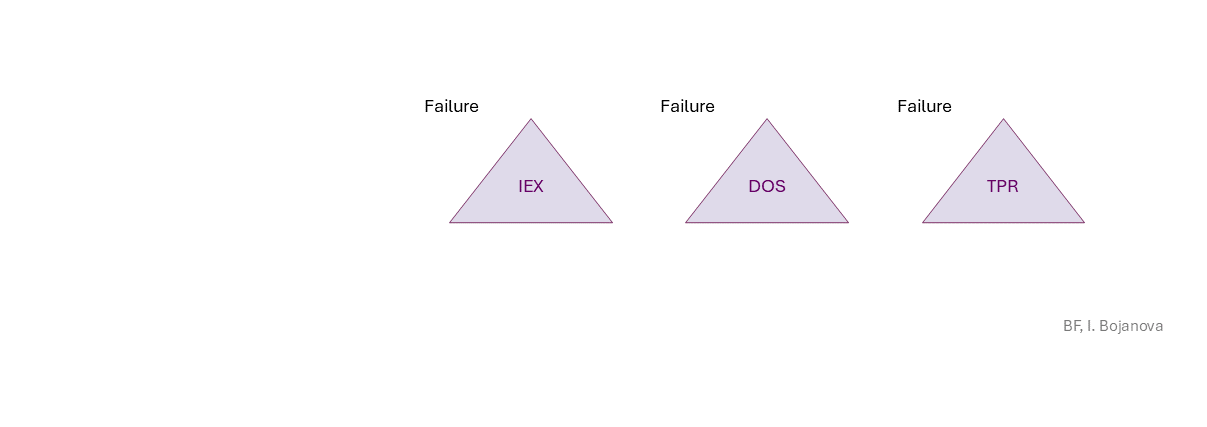
Information Exposure (IEX) (confidentiality loss),Denial of Service (DOS) (availability loss),Data Tampering (TPR) (integrity loss) security failure.
|
| Class | Definition |
| DVL | Data Validation (DVL) class – Data are validated (i.e., syntax check) or sanitized (i.e., escape, filter, or repair) improperly. |
| Operation | Definition |
| Validate | Validate operation – Check data syntax (e.g., proper form/grammar or missing symbols/elements) in order to accept or sanitize it. |
| Cause/Consequence | Definition |
| Code Bug | Code Bug type – An error in the implementation of an operation – proper operands over an improper operation. It is the roor cause of a security vulnerability. Must be fixed to resolve the vulnerability. |
| Erroneous Code | Erroneous Code bug - There is a coding error in the implementation of the operation. |
| Injection Final Error | Injection final error/exploit vector type – An exploitable or undefined system behavior caused by validation or sanitization bugs. |
| File Injection | File Injection final error – Maliciously inserted data (e.g., with .. and / or with file entries) into an input used to access/modify files or as a file content. |
| Operation Attribute | Definition |
| Mechanism | Mechanism operation attribute type – Shows how the operation with a bug or faulty operand is performed. |
| Format | Format operation attribute – The operation is via a policy based on syntax format (e.g., defined via regular expression). |
| Source Code | Source Code operation attribute type – Shows where the code of the operation with a bug or faulty operand resides within the software, firmware, or hardware. |
| Codebase | Codebase operation attribute – The operation is in the programmer's code - in the application itself. |
| Execution Space | Execution Space operation attribute type – Shows where the operation with a bug or faulty operand is executed and the privilege level at which it runs. |
| Local | Local operation attribute – The bugged code runs in an environment with access control policy with limited (local user) permission. |
| Operand Attribute | Definition |
| Data State | Data State operand attribute type – Shows where the data comes from. |
| Entered | Entered operand attribute – Data are from a user via a user interface (e.g., input field, dialog or a command prompt). |
| Failure | Definition |
| IEX | Information Exposure (IEX) – Inadvertent disclosure of information that leads to confidentiality loss. |
| DOS | Denial of Service (DOS) – Disruption of access to or use of information or information systems that leads to availability loss. |
| TPR | Data Tampering (TPR) – Unauthorized modification or destruction of information that leads to integrity loss. |